RSA Public-Key Encryption
- RSA Public-Key Encryption
- Motivation and Introduction
- -th Roots in a Group
- Description of RSA
- On the Security of RSA
- Digital Signatures
RSA Public-Key Encryption
(Copied/paraphrased/annotated from the script on Discrete Mathematics HS21 by Prof. Ueli Maurer)
Motivation and Introduction
The RSA public-key cryptosystem, invented in 1977 by Rivest, Shamir, and Adleman (R. L. Rivest, A. Shamir, and L. Adleman, A method for obtaining digital signatures and publickey cryptosystems, Communications of the ACM, Vol. 21, No. 2, pp. 120–126, 1978.), is used in many security protocols on the Internet, for instance in TLS/SSL. Like the Diffie-Hellman protocol (Diffie-Hellman Key-Agreement) it allows two parties to communicate securely, even if the communication channel is insecure, provided only that they can authenticate each other’s public keys (respectively the Diffie-Hellman values). Moreover, the RSA system can be used as a digital signature scheme (see below). RSA was the first cryptographic system offering this important functionality.
-th Roots in a Group
Recall Lagrange’s theorem:
📖 Lagrange’s Theorem: Let be a finite group and let be a subgroup of . Then the order of divides the order of , i.e., divides .
To understand the RSA system, all we need is the following simple theorem which is a consequence of Lagrange’s theorem.
📖 -th Roots in a Group: Let be some finite group (multiplicatively written), and let be relatively prime to (i.e., ). The function is a bijection and the (unique) -th root of , namely satisfying , is
where is the multiplicative inverse of modulo , i.e.,
Proof: We have for some . Thus, for any we have
because of the following corollary we stated earlier:
📎 Let be a finite group. Then for every .
This thus means that the function is the inverse function of the function (which is hence a bijection). Thus the theorem about -th roots in a group has been proven.
Description of RSA
Motivated by the Diffie-Hellman protocol also based on modular exponentiation, Rivest, Shamir and Adleman suggested as a possible class of groups the groups , where is the product of two sufficiently large secret primes and . Recall that is the Euler function mentioned earlier:
💡 The Euler function is defined as the cardinality of (known as Euler’s totient function or Euler’s phi function):
Also recall that its value can be computed using the prime factorization of its argument:
📌 If the prime factorization of is , then
The order of ,
can thus only be computed if the prime factors and of are known. The (public) encryption transformation is defined by
and the (secret) decryption transformation is defined by
where can be computed according to
The RSA public-key cryptosystem is summarized in the following figure. Note, that this is one-way only, Alice will receive an encrypted message from Bob and will be able to decrypt it. One would also need to mirror the setup to enable two-way encrypted communication also from Alice to Bob.
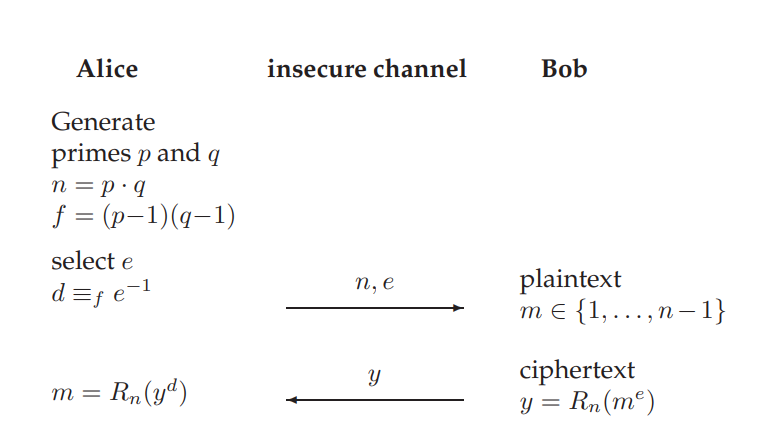
The RSA system is usually (for instance in the TLS/SSL protocol) used only for key management, not for encrypting actual application data. The message is an encryption key (typically a short-term session key) for a conventional cryptosystem which is used to encrypt the actual application data (e.g. of a TLS session).
On the Security of RSA
Let us have a brief look at the security of the RSA public-key system. It is not known whether computing -th roots modulo (when ) is easier than factoring , but it is widely believed that the two problems are computationally equivalent. Factoring large integers is believed to be computationally infeasible. If no significant breakthrough in factoring is achieved and if processor speeds keep improving at the same rate as they are now (using the so-called Moore’s law), a modulus with 2048 bits appears to be secure for the next 15 years, and larger moduli (e.q. 8192 bits) are secure for a very long time.
Obviously, the system is insecure unless Bob can make sure he obtains the correct public key from Alice rather than a public key generated by an adversary and posted in the name of Alice. in other words, the public key must be sent from Alice to Bob via an authenticated channel. This is usually achieved (indirectly) by using a so-called public-key certificate signed by a trusted certification authority. One also uses the term public-key infrastructure (PKI).
It is important to point out that for a public-key system to be secure, the message must be randomized in an appropriate manner. Otherwise, when given an encrypted message, an adversary can check plaintext messages by encrypting them and comparing them with the given encrypted message. If the message space is small (e.g. a bit), then this would allow to efficiently break the system.
Digital Signatures
The RSA system can also be used for generating digital signatures. A digital signature can only be generated by the entity knowing the secret key, but it can be verified by anyone, e.g. by a judge, knowing the public key. Alice’s signature for a message is
where denotes concatenation and is a suitable function introducing redundancy into the message and the string is naturally understood as an element of . A signature can be verified by raising it to the -th power modulo and checking that it is of the correct form . The message is recovered from the signature.